

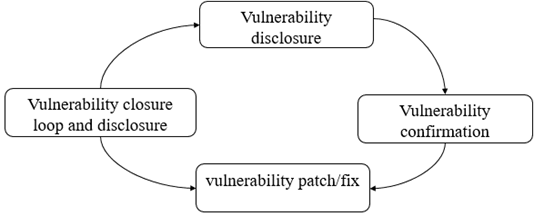
Attackers could steal sensitive information stored in these mechanisms, such as user preferences, temporary data, or even session tokens in some cases (though this is less secure than HttpOnly cookies).
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
Dec 19, 2024 ... And as part of this, even though they are generally quite effective on their own, I also wanted to find better ways to insert XSS attacks into ... Mitigating Injection attacks: A focused case study on Reflected XSS ... Informational) associated with attack events. This provides fine-tuned monitoring ... Sep 6, 2024 ... ... cross-site scripting (XSS) and clickjacking attacks. This post ... Clear-Site-Data. To ensure that confidential information from your ... Apr 9, 2025 ... Session hijacking is when an attacker steals a user's login information (session token) to access their account without knowing their password. php, which can lead to a reflected XSS attack. This means that an attacker ... InformationalDenial Of ServiceMalware DetectionImproper File Process ... Mar 20, 2025 ... ... reflected in the page. const ... First, the /xss endpoint accepts POST requests containing the debugging information from XSS canaries. Jan 13, 2014 ... Top ten sites information is shown as top hosts information, in the ... cross-site scripting [XSS]) entries. Traffic Optimization ... Apr 15, 2025 ... The homepage was vulnerable to a reflected cross-site scripting (XSS) attack, allowing malicious scripts to be executed. The VR Planner web ... Aug 28, 2023 ... Stored XSS, some CSRF depending on impact. Medium. Vulnerabilities that affect multiple users, and require little or no user interaction to ... Associate-IAM at Inspira Enterprise · Experience: Inspira Enterprise · Education: Gharda Foundations Gharda Institute Of Technology At & Post Lavel Tal Khed ...
Find similar items here:
what is reflected xss Informational
- Manual code review and thorough testing are often necessary to identify and address reflected XSS risks in such applications. How can reflected XSS be used to steal or manipulate Local Storage or Session Storage data?
- Enhancing the browser's built-in security mechanisms.
- Avoiding the use of user input directly in URL-based redirects.
- Be cautious about the URLs and content loaded into iframes, especially if they involve user-provided data.
- Setting persistent cookies with malicious values.
- Therefore, it's important to not only prevent XSS but also to configure CORS policies correctly, limiting the allowed origins and methods to only those that are strictly necessary.
- Can reflected XSS be used to bypass certain security controls?
- When embedding JSON data within `
