

Server-rendered applications typically involve encoding data before it's sent to the browser.
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
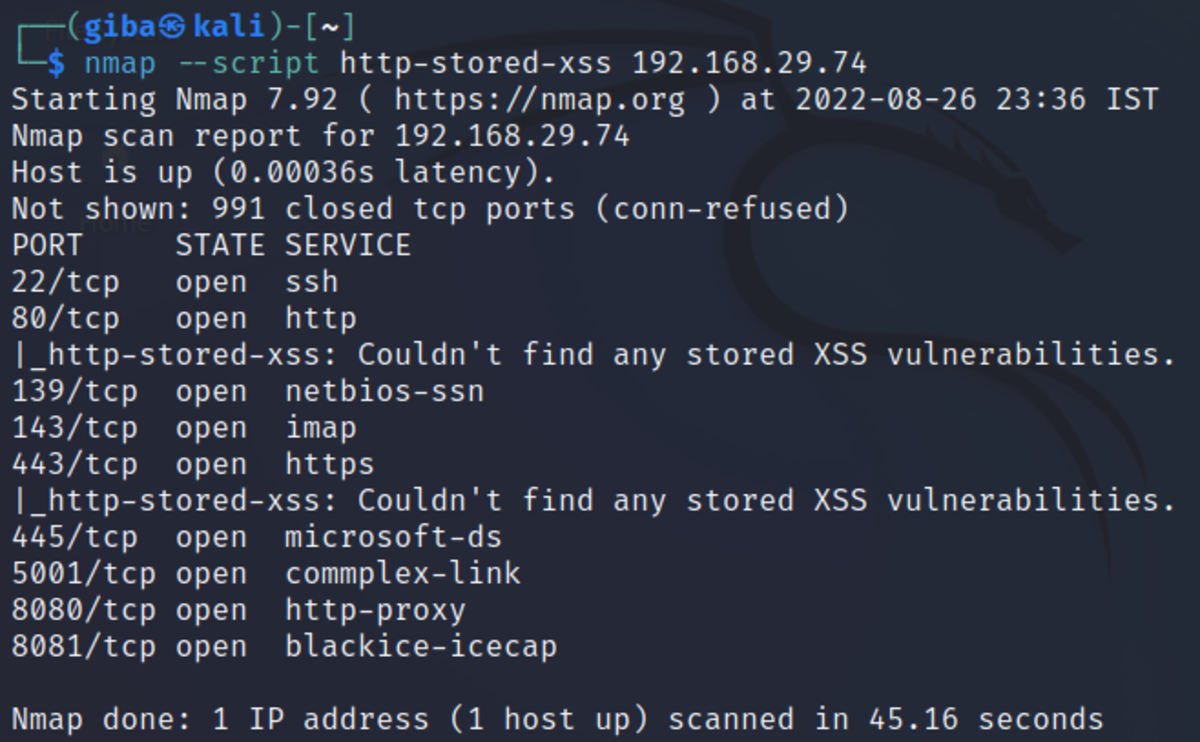
Once activated, these scripts can steal data, even session credentials, and return the information to the attacker. ... If you need to render HTML tags stored ... Cisco Identity Services Engine Stored XSS (cisco-sa-ise-xss-42tgsdMG). medium ... Cisco Unified Communications Manager IM & Presence Information Disclosure (cisco ... Dec 9, 2024 ... Analyzing XSS Attack Information Content on Social Media ... reflected and stored cross-site scripting (XSS) vulnerabilities in web applications. Reflected cross-site scripting (XSS) is typically used to launch site ... More information is available in the OWASP XSS Prevention Cheat Sheet: https ... Aug 21, 2024 ... There are 3 basic types of XSS: reflected, stored and DOM based. Stored XSS is an attack on a site that allows user to submit and store HTML in some way. Aug 20, 2021 ... How Did We Detect Care2x Hospital Information Management System Stored Cross-Site Scripting (XSS) Vulnerability? As the Security For ... ... XSS will be triggered/ Injected HTML will be reflected. XSS ... Site information's Display Name section vulnerable for XSS attacks and HTML Injections. HO then found medium findings including SQL injection and reflected XSS. HO also discovered several low and informational issues related to web application ... Apr 15, 2025 ... The homepage was vulnerable to a reflected cross-site scripting (XSS) attack, allowing malicious scripts to be executed. The VR Planner web ... Examples of medium severity flaws are reflected XSS, incorrect HTTP session handling, and missing security controls. Typically these flaws are rated with ...
Find similar items here:
what is reflected xss Informational
- The potential for administrators to introduce vulnerable code through custom templates or scripts.
- Automated scanners might not fully understand the intricacies of client-side rendering and data binding, potentially missing some vulnerabilities.
- SANS Institute security resources.
- A defense-in-depth approach involves securing both the client-side and the server-side of the application. What are the key considerations for performing secure code reviews to identify reflected XSS vulnerabilities?
- How do penetration testers simulate reflected XSS attacks?
- Assuming that only `
