
Anomaly Detection What are some common security threats that IPsec can help protect against?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
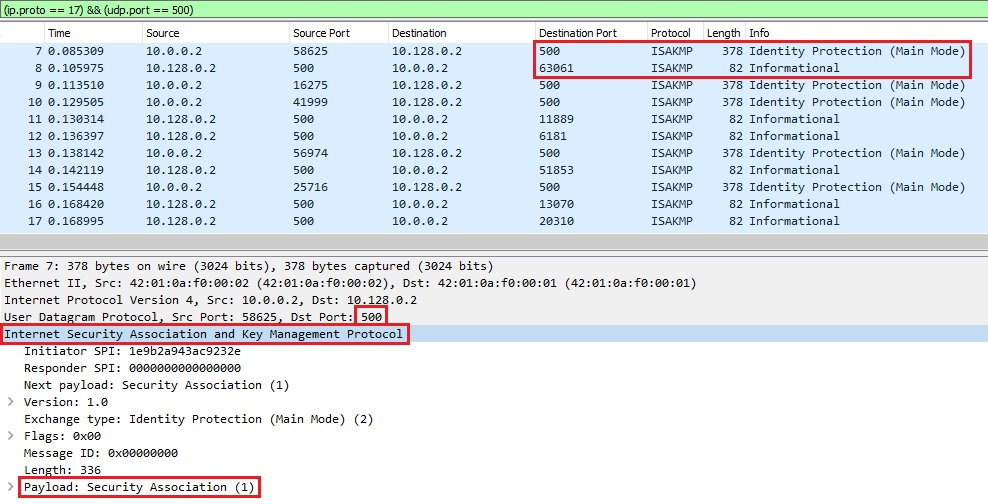
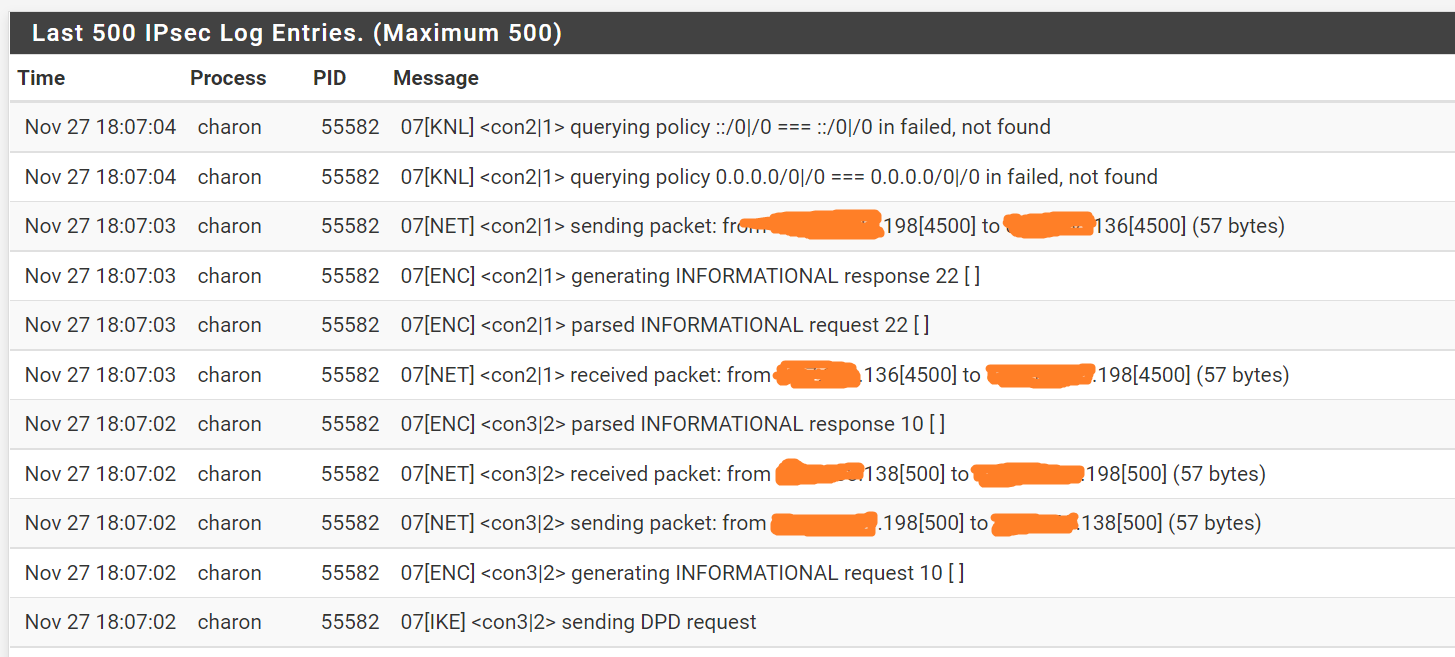
2 22:30:09,305497& ... Dec 28, 2011 ... I have StrongSwan running on a ubuntu server and I'm trying to create an ipsec encrypted VPN tunnel with a Cisco 2821 router. The connection is not working. An ESP packet consists of an ESP header, the encrypted IP payload body and an ESP trailer needed for padding. The Authentication Data field appended at the end ... Nov 1, 2018 ... But no data arrives on the strongSwan client side. I checked that using tcpdump by forwarding the decapsulated ipsec traffice to the NFLOG chain ... Sep 30, 2008 ... Setting up an IOS router to utilize IPsec starts with the configuration of the ISAKMP policy and the router's ISAKMP authentication key data. Quick Mode negotiates the SA for the data encryption and manages the key exchange for that IPSec SA. IKE Glossary. A security association (SA) is the ... Jan 5, 2025 ... VPNs protect your information through varying encryption methods and security protocols. Find out what each VPN uses and what you need to be ... • Basic concepts of information security and data protection. • Mathematical ... • Basics of network security (IPsec, HTTPS, TLS). • Reactive security ... To configure EMS for this use case: · Go to Endpoint Profiles > Remote Access. · Select the desired profile. · In XML view, configure the following for the ... Jan 26, 2011 ... I'm getting the below issue when configuring a site 2 site ipsec VPN, unfortunately I only have control over 1 end so I'm just copying the config from the ...
Find similar items here:
what is ipsec Informational
- Security Zones
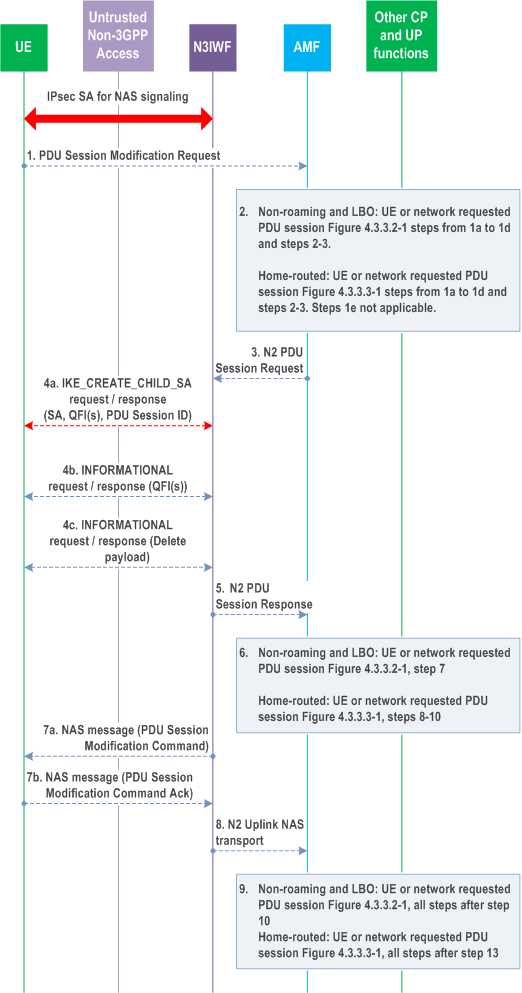
- Feature Sets How does IPsec support remote access VPNs for individual users connecting from untrusted networks?
- Built-in NAT-T Support
- Tunnel Management What are some common tools used for IPsec management and monitoring?
- Algorithm Suites
- Improved Security How does IKEv2 handle NAT traversal?
- Configuration Management Tools
- Header Modifications
- Tunneling Overhead How does IPsec handle the encryption and authentication of data packets in both transport and tunnel modes?
- Transform Sets
-
Next Day Delivery by USPS
Find out more
Order by 9pm (excludes Public holidays)
$11.99
-
Express Delivery - 48 Hours
Find out more
Order by 9pm (excludes Public holidays)
$9.99
-
Standard Delivery $6.99 Find out more
Delivered within 3 - 7 days (excludes Public holidays).
-
Store Delivery $6.99 Find out more
Delivered to your chosen store within 3-7 days
Spend over $400 (excluding delivery charge) to get a $20 voucher to spend in-store -
International Delivery Find out more
International Delivery is available for this product. The cost and delivery time depend on the country.
You can now return your online order in a few easy steps. Select your preferred tracked returns service. We have print at home, paperless and collection options available.
You have 28 days to return your order from the date it’s delivered. Exclusions apply.
View our full Returns and Exchanges information.
Our extended Christmas returns policy runs from 28th October until 5th January 2025, all items purchased online during this time can be returned for a full refund.
No reviews yet. Only logged in customers who have purchased this product may leave a review.
