

What are software composition analysis (SCA) tools?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
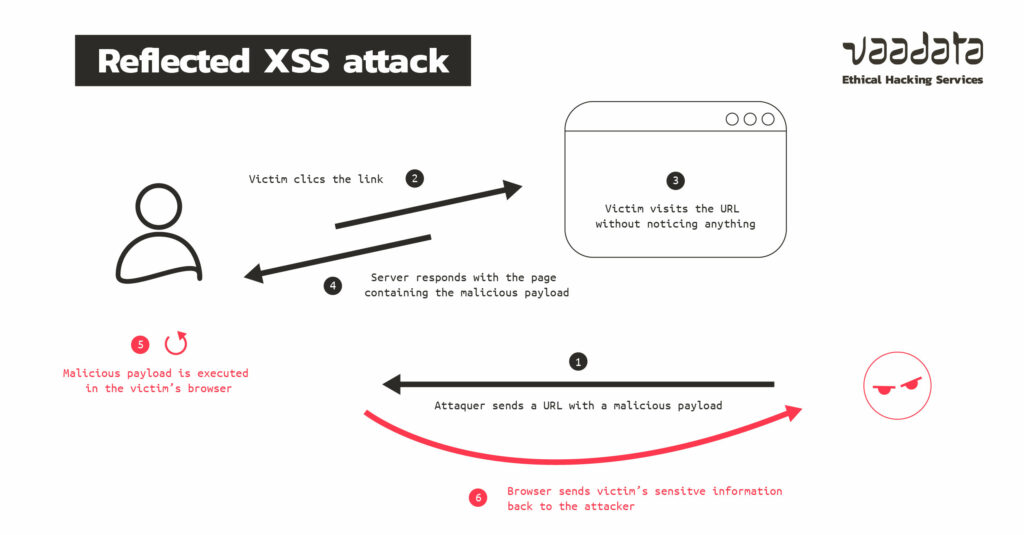
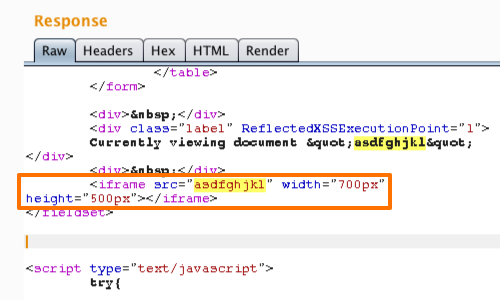
CSRF and XSS are two such client-side attacks. They both are nefarious and have serious outcomes. Both involve injecting ill-intent contents into the end-user' ... In order for an XSS attack to be successful, an attacker must be able to insert and execute malicious content in a webpage. Thus, all variables in a web ... Apr 16, 2025 ... XSS is not an exploit or a tactic — it is a precondition for exploitation. In frameworks like MITRE ATT&CK, it maps to T1059.007 (Command and ... Apr 10, 2025 ... Cross-site scripting (XSS). A cross-site scripting (XSS) attack is one in which an attacker is able to get a target site to execute malicious ... Mar 8, 2022 ... Cross-site scripting (XSS) is a cyberattack in which a hacker enters malicious code into a web form or web application url. Cross-site scripting (XSS) is a form of cyber attack where a malicious actor injects harmful executable scripts into the code of a trusted website or ... Feb 20, 2015 ... I decided to take a quick look at Zoho:s android-application. Zoho is a mail-service and has around 13 million users worldwide. They have a reputation of ... Reflected XSS attack example. While visiting a forum site that requires users to log in to their account, a perpetrator executes this search query
