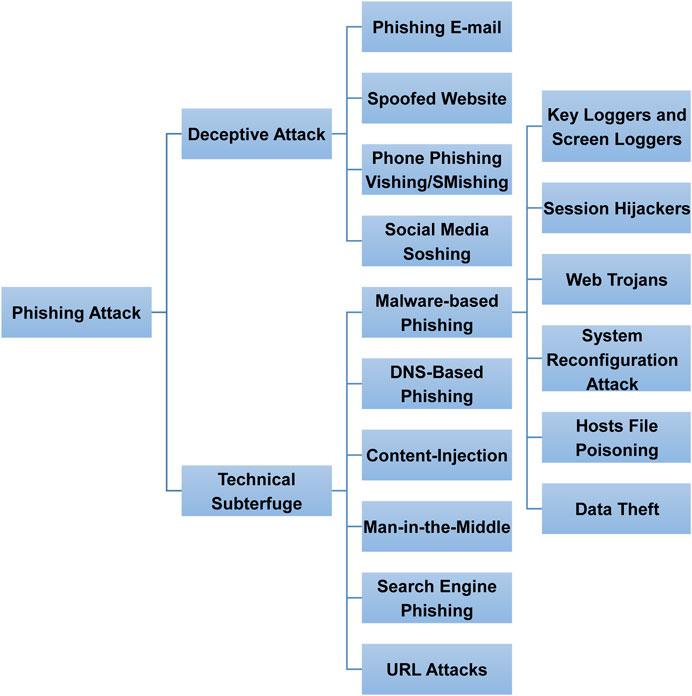



What are the IPv6 equivalents of ARP spoofing techniques? How can ARP spoofing be used to manipulate routing tables?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
Find similar items here:
what is the aim of an arp spoofing attack Informational
- How can attackers leverage ARP spoofing to cause failures or misconfigurations in load balancers? What is the aim of an attacker using ARP spoofing to conduct a replay attack?
- How does ARP spoofing facilitate the redirection of name resolution requests to an attacker-controlled host?
- How can attackers leverage ARP spoofing to manipulate network paths or cause routing instability? What is the aim of an attacker using ARP spoofing to conduct a malicious firmware update attack on endpoints?
- How can attackers redirect traffic by manipulating routing information? What is the aim of an attacker who wants to gain access to internal network resources via ARP spoofing?
- What is the relationship between ARP spoofing and compromising the integrity and security of endpoint devices at a low level? How can ARP spoofing be used to target network devices that perform deep flow inspection (DFI)?
- What are the unique characteristics of ARP spoofing? What is the aim of an attacker using ARP spoofing against network infrastructure devices like routers and switches?
- How can an attacker silently observe network traffic using ARP spoofing? What is the impact of a successful ARP spoofing attack on network performance?
- How can attackers leverage ARP spoofing to alter device configurations? What is the aim of an attacker using ARP spoofing to disrupt communication in cloud environments?
- What role does ARP spoofing play in generating inaccurate or incomplete network traffic records?
- What is the relationship between ARP spoofing and exploiting vulnerabilities related to data type limits? How can ARP spoofing be used to target network protocol analyzers?
-
Next Day Delivery by USPS
Find out more
Order by 9pm (excludes Public holidays)
$11.99
-
Express Delivery - 48 Hours
Find out more
Order by 9pm (excludes Public holidays)
$9.99
-
Standard Delivery $6.99 Find out more
Delivered within 3 - 7 days (excludes Public holidays).
-
Store Delivery $6.99 Find out more
Delivered to your chosen store within 3-7 days
Spend over $400 (excluding delivery charge) to get a $20 voucher to spend in-store -
International Delivery Find out more
International Delivery is available for this product. The cost and delivery time depend on the country.
You can now return your online order in a few easy steps. Select your preferred tracked returns service. We have print at home, paperless and collection options available.
You have 28 days to return your order from the date it’s delivered. Exclusions apply.
View our full Returns and Exchanges information.
Our extended Christmas returns policy runs from 28th October until 5th January 2025, all items purchased online during this time can be returned for a full refund.
No reviews yet. Only logged in customers who have purchased this product may leave a review.
