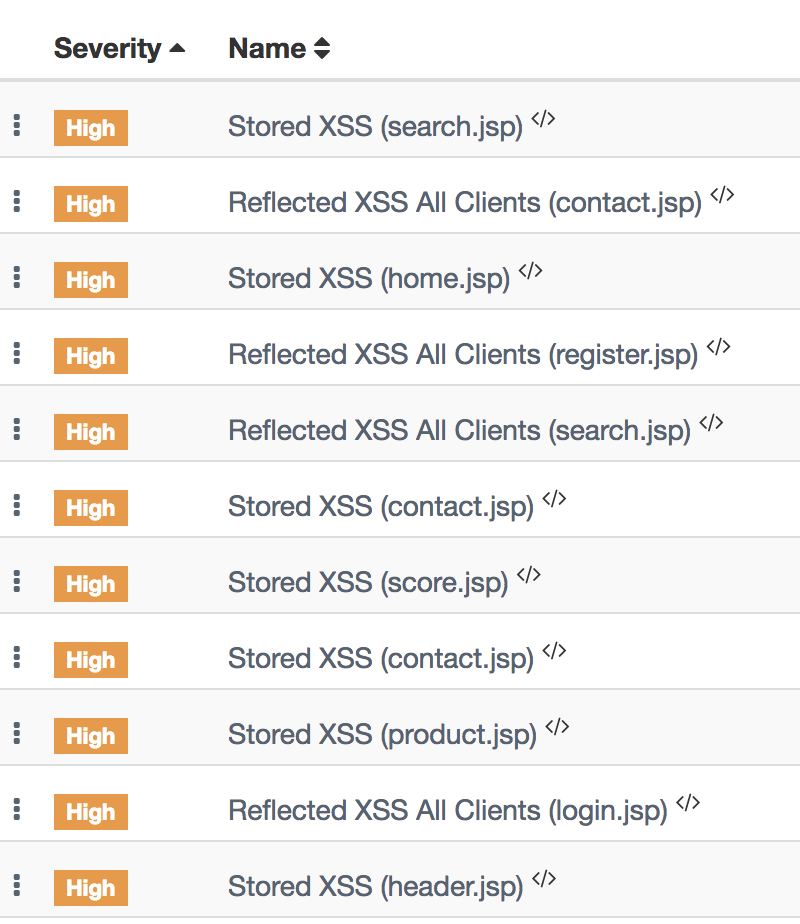

What is the role of web application firewalls (WAFs) in preventing reflected XSS?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
retrieves the malicious script from the server when it requests the stored information. Stored XSS is also sometimes referred to as Persistent or Type-I XSS. Mar 8, 2025 ... DOM-Based. The main difference between Reflected and Stored XSS compared to DOM-Based XSS ... informational purposes only. While I always ... Feb 26, 2024 ... Stored XSS, reflected XSS, and DOM-based XSS are the three most common ... stored login information. XSS Attacks Are Time-Consuming ... May 3, 2020 ... Stealing private information with XSS – Reflected XSS – Bypass WAF. Cross-Site Scripting. (XSS). 2. P3. Resolved. Social media account ... Jul 11, 2023 ... Attempting to exploit vulnerabilities found and access confidential information that may be stored on systems. ○ Documenting and reporting on ... Aug 1, 2023 ... A reflected cross-site scripting (XSS) vulnerability exists in Brocade Webtools PortSetting.html of Brocade Fabric OS version before Brocade Fabric OS v9.2.0 The two basic types of XSS attacks are: • Reflected XSS. • Stored XSS. In reflected XSS, a user is somehow lured to send malicious code to server. The server ... INFORMATIONAL. 1. 2. 2. 2. 1. FINDING. SEVERITY. SQL Injection x 3. CRITICAL. IDORs. HIGH. Stored XSS. HIGH. Reflected XSS. MEDIUM. Information Disclosure. Vulnerabilities that require interaction to obtain user identity information, including but not limited to stored XSS vulnerabilities;. Arbitrary file ... Jan 14, 2021 ... The article is informational. Do not break the law. XSS have various variations, for example, a forum post with the text
