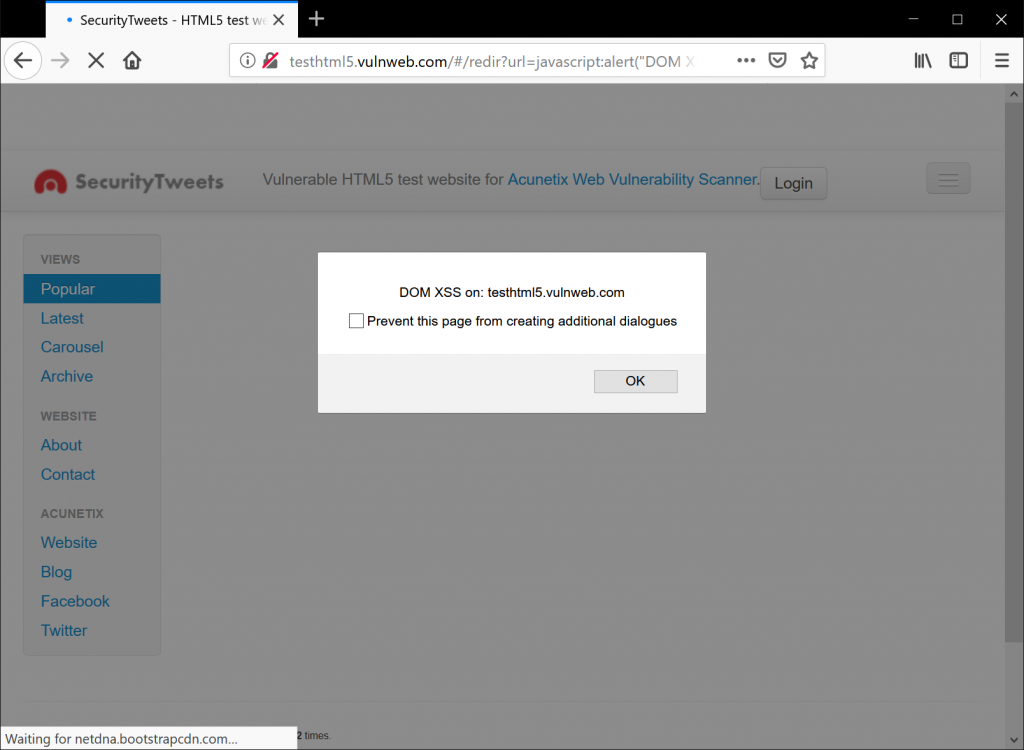


What are the prerequisites for a reflected XSS attack?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
Apr 8, 2024 ... During the Penetration process, XSS, Cookie Stealing via Stored XSS, Discovery of Informational Files in the. Root Server Directory, Moodle ... Jun 26, 2024 ... ... Cross Site Scripting (XSS) and the common flavours it comes in; Stored and Reflected XSS. To give a brief overview of each type: Stored ... Nov 14, 2023 ... Stored XSS attacks: These ... When the victim makes a request for the stored data, the server returns the malicious script. Reflected XSS ... Oct 23, 2017 ... @juhakivekas @davewichers would you rather that the alert was raised at LOW or INFORMATIONAL risk? (When the response is json.) ... Once activated, these scripts can steal data, even session credentials, and return the information to the attacker. ... If you need to render HTML tags stored ... Reflected cross-site scripting (XSS) is typically used to launch site ... More information is available in the OWASP XSS Prevention Cheat Sheet: https ... Apr 10, 2025 ... Provides the browser with a token identifying the reporting endpoint or group of endpoints to send CSP violation information to. The endpoints ... Sep 13, 2011 ... A cross-site scripting, information ... Seeker automatic application security testing solution for reporting the Contact Details Reflected XSS ... (#1703); + Reflected XSS requiring user interaction on search. (#1705); + ... Informational tooltips added + option to disable them in config file if ... Jan 14, 2021 ... The article is informational. Do not break the law. XSS have various variations, for example, a forum post with the text
