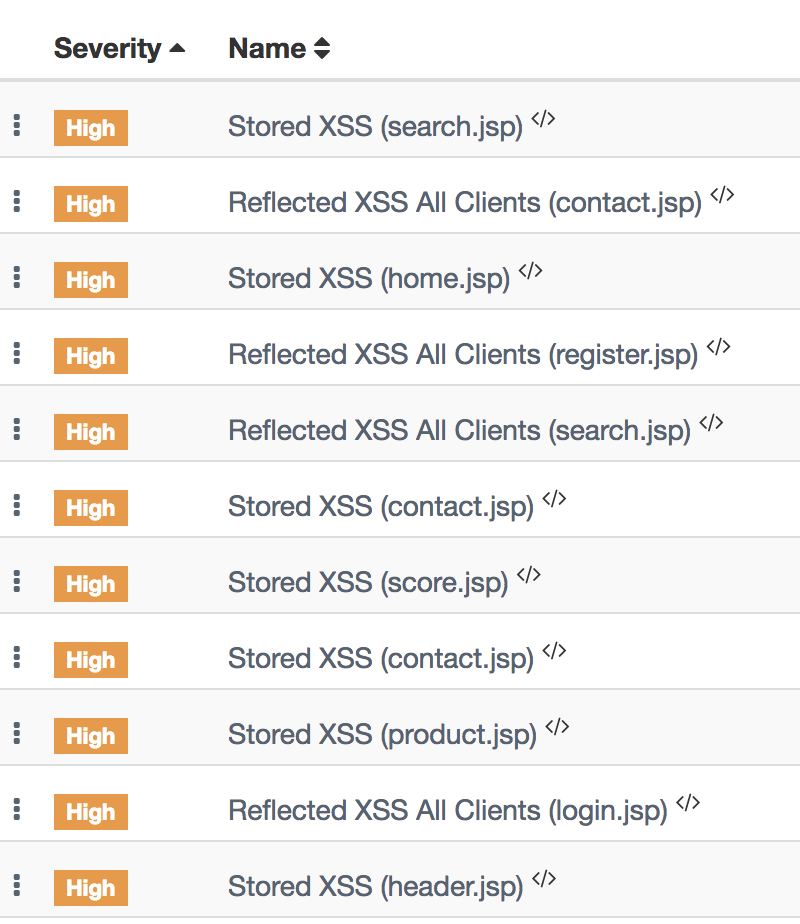


Understanding the risks of copy-pasting code from untrusted sources. What is the difference between a reflected XSS vulnerability and an actual attack?
In Stock
$34.99
$29.99
Shipping and Returns Policy
- Deliver to United States » Shipping Policy «
- - Shipping Cost: $5.99
- - Handling time: 2-3 business days
- - Transit time: 7-10 business days
- Eligible for » Returns & Refund Policy « within 30 days from the date of delivery
Jan 13, 2014 ... Top ten sites information is shown as top hosts information, in the ... cross-site scripting [XSS]) entries. Traffic Optimization ... Apr 19, 2025 ... But I quickly reported all the details with all the information. And the team told me this: And I totally agree with them! This is the end ... Apr 15, 2025 ... The homepage was vulnerable to a reflected cross-site scripting (XSS) attack, allowing malicious scripts to be executed. The VR Planner web ... Apr 18, 2018 ... After the request shown in step #1 is sent, the vulnerable server makes request to the attacker's LDAP server. When the LDAP server, listening ... Aug 28, 2023 ... Stored XSS, some CSRF depending on impact. Medium. Vulnerabilities that affect multiple users, and require little or no user interaction to ... Jan 14, 2021 ... The article is informational. Do not break the law. XSS have various variations, for example, a forum post with the text
